Security Advisories
The Alcatel-Lucent Enterprise Product Security Incident Response Team (ALE PSIRT) is dedicated to managing requests, investigating and reporting vulnerabilities or technical issues impacting our products and solutions.

We understand how important secure products and solutions are to our customers. It is our goal to ensure that Alcatel-Lucent Enterprise products are developed with all the appropriate security principles at the foundation. We follow a comprehensive security program that combines:
-
- Secure software development best practices, processes and tools
-
- Rigorous product security requirements
-
- Periodic validation and quality of security testing before release
Despite these security principles and related actions, vulnerabilities can be discovered in the product software components which, when exploited, can have an impact on the security level of the products once deployed in a customer's networks.
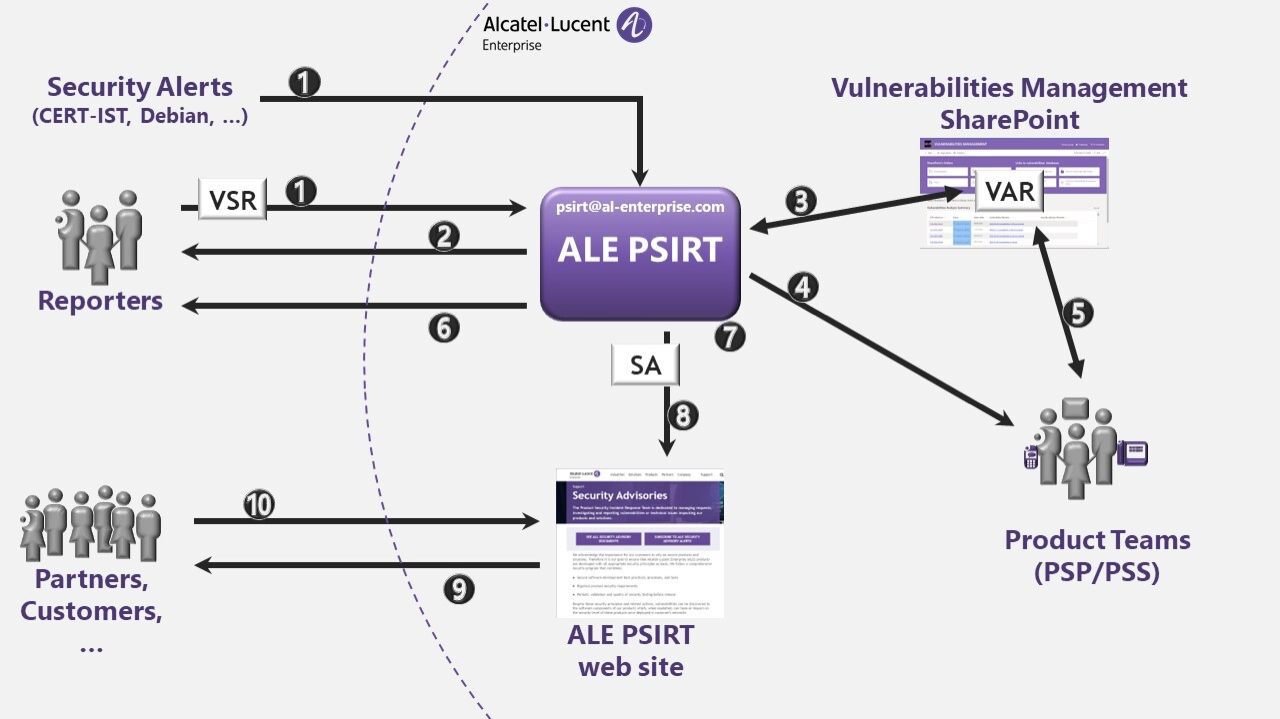
Product security incident response process summary
-
1. The ALE PSIRT receives a security alert or, a reporter (Business Partner, customer, …) sends a potential vulnerability described in a Vulnerability Summary Report (VSR) to the ALE PSIRT (PSIRT@al-enterprise.com)。
-
2. The ALE PSIRT acknowledges receipt of the VSR to the reporter.
-
3. The ALE PSIRT analyses the relevancy of the vulnerability in ALE context in terms of if there is a risk for ALE products. A Vulnerability Analysis Report (VAR) is created within the internal Vulnerabilities Management SharePoint. The VAR will be the reference for the ALE PSIRT to follow the analysis as it advances through the process. The criticality of the vulnerability is reassessed following the Common Vulnerability Scoring System Version 3.1 Calculator.
-
4. The ALE PSIRT notifies the Vulnerabilities Analysis Team (the PSP and the PSS) about the VAR.
-
5. The Product Security Prime completes the VAR, indicating the vulnerability status regarding the product. There may be multiple steps required that provide temporary steps to address the problem (through configuration, imposing a restriction, or finding a work-around), before a final resolution is found.
-
6. The reporter will be informed, on a regular basis, about the ongoing vulnerability investigation. Most notably, the ALE PSIRT will communicate the conclusion of the analysis to the reporter.
-
7. If any impacts are confirmed, and when there is a remediation, the ALE PSIRT will coordinate a fix and impact assessment, and define, together with the product line team, the resolution delivery timeframe, notification plans and disclosure to public organisations such as mitre.org and CERT organisations. When there is sufficient information to communicate, the Security Advisories Committee will request the creation or update of a Security Advisory (SA).
-
8. The ALE PSIRT will publish the SA on ALE PSIRT web site, to inform external ALE concerned parties such as Partners and customers.
-
9. The ALE PSIRT mailing list subscribers receive notification about the published SA. Anyone can subscribe to the mailing list from the ALE PSIRT web site.
-
10. Anyone interested can go to the ALE PSIRT web site and read the Security Advisories.
How to report a suspected security vulnerability
Individuals or organisations experiencing technical security issues with an ALE product or solution are strongly encouraged to report the issues by contacting the ALE PSIRT using following these steps:
-
1. Complete the Vulnerability Summary Report (VSR)。
-
2. Send the completed report to the email address: PSIRT@al-enterprise.com
-
3. For confidentiality reason, please consider using the ALE PGP public key
The ALE PSIRT process will be followed while maintaining the discussion with the reporter. Communication with all involved parties is a key activity in our vulnerability solution process.
Alcatel-Lucent Enterprise customers can also report suspected security vulnerabilities through their usual support channels. Depending on the customer maintenance contract, these contact points will be able to assist in more general situations such as providing:
-
- Technical assistance to determine if a security problem exists
-
- Configuring an ALE product for a specific security-related function
-
- Answers about an announced security problem with an ALE product
-
- Implementation of any workarounds to avoid a vulnerability
Confidentiality - ALE PSIRT PGP public key:
ALE PSIRT process ensures that neither unauthorised ALE employees nor outside users will get access to the information provided by the incident reporter. ALE also guarantees that on request, the name of the incident reporter will not be disclosed in public communications or be used in further external distribution. Similarly, the ALE PSIRT asks incident reporters to maintain strict confidentiality until complete resolutions are available for customers and have been published by the ALE PSIRT on the ALE websites through the appropriate coordinated disclosure. For ensuring the confidentiality of the reporting and following steps of communication with ALE PSIRT, we encourage sending encrypted messages using the ALE PGP public key and sending in return the public PGP key of the incident reporter.
-
- E-mail: PSIRT@al-enterprise.com
-
- The public key can be found on https://keyserver.pgp.com
Note that ALE PSIRT should NOT be contacted to report or get support for security incidents that are happening "live" in deployed networks and solutions. Such incidents are to be reported only through the usual customer support channels.
Third-party software vulnerabilities
ALE PSIRT works with third-party coordination centres such as CERT-IST, NVD and US-CERT to manage vulnerabilities notices reported on third-party software embedded or used in ALE products and solutions. The reports are referred to with a unique Common Vulnerabilities and Exposures (CVE) number. Each CVE issued is analysed by ALE teams to provide an adjusted risk score that reflects the effective impact on our products.
Severity assessment
When the vulnerability is discovered, internally or externally, through pentests, CERT reports, or from the field, it is important to qualify the vulnerability within the context of ALE products.
To help this qualification process ALE uses a tool developed by the FIRST organisation called the CVSS version 3.1 calculator.
By answering a number of questions, a new score is established for the vulnerability.
The requalified score is called the ALE Vulnerability Scoring System (AVSS).
| Rating | CVSS/AVSS Score |
|---|---|
| Not impacted | 0.0 |
| Low | 0.1 - 3.9 |
| Medium | 4.0 - 6.9 |
| High | 7.0 - 8.9 |
| Critical | 9.0 - 10.0 |
Security advisory disclosure
If one or more of the following conditions exist, ALE will publicly disclose a Security Advisory:
-
1. An incident response process has been completed and it has been determined that sufficient software patches or workarounds exist to address the vulnerability, or subsequent public disclosure of code fixes is planned to address high to critical severity vulnerabilities.
-
2. An active exploitation of the vulnerability has been observed that could lead to increased risk for our customers. Early Security Advisories may then be published prior to the publication of available patches or corrections to inform our customers about potential risks.
-
3. Public information about the vulnerability can expose our customers to potential increased risk. Early Security Advisories may then be published prior to the publication of available patches or corrections to inform our customers about potential risks.
ALE reserves the right to deviate from this policy on an exception basis to ensure software patch availability and our customers' security.